Unverified software downloads: A significant risk to server security
Debian started signing their repository packages way back in 2007 with the release of Debian 4.0. Yet somehow we have gone backwards when it comes to validation of downloaded software in recent years.
Most software these days, whether they be package managers for programming languages or container tools that download images, don’t validate the cryptographic integrity of downloads. Downloading over TLS alone is insufficient to protect you against supply chain attacks. Someone who can manage to break into the download server will be able to add a backdoor to the binary. Xubuntu servers got compromised recently and was found serving malware.
In many cases, the download might be happening from a nearby mirror or a CDN. While the upstream project might have good security practices for securing their servers, the same could not be said of the mirror operators.
In some cases, tools produce misleading output. Here in the screenshot below, bastille (a jail manager for FreeBSD) claims that it has validated the checksum. The validation is done by downloading a MANIFEST text file from the same directory as the software and comparing the checksum of the binary with the contents of the text file.
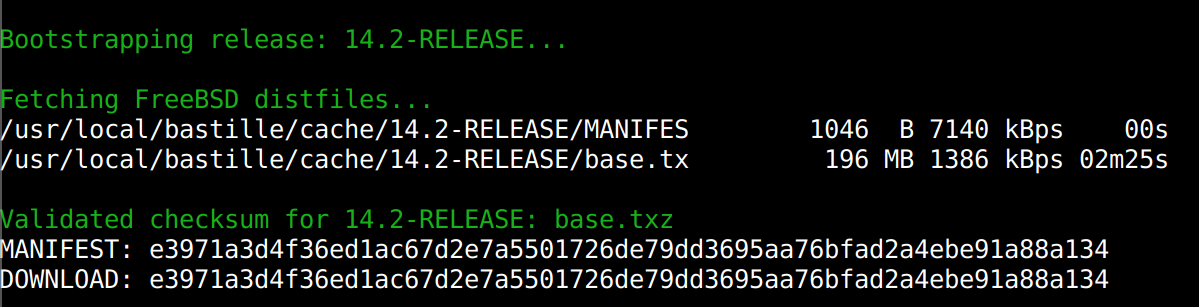 |
While it will protect you against corrupted downloads, it will not save you from a malicious binary. Although it technically does validate the checksum, my personal expectation is that the tool would have had verified the GPG signature of the binary.
In the absolute worst case, some tools download software over unencrypted HTTP without any cryptographic signature verification whatsoever.
Developers also need to be trained to verify downloads before use. The following is a screenshot from the FreeBSD handbook for setting up a jail. The documentation needs to be updated to encourage people to verify the downloads like how OpenWrt does
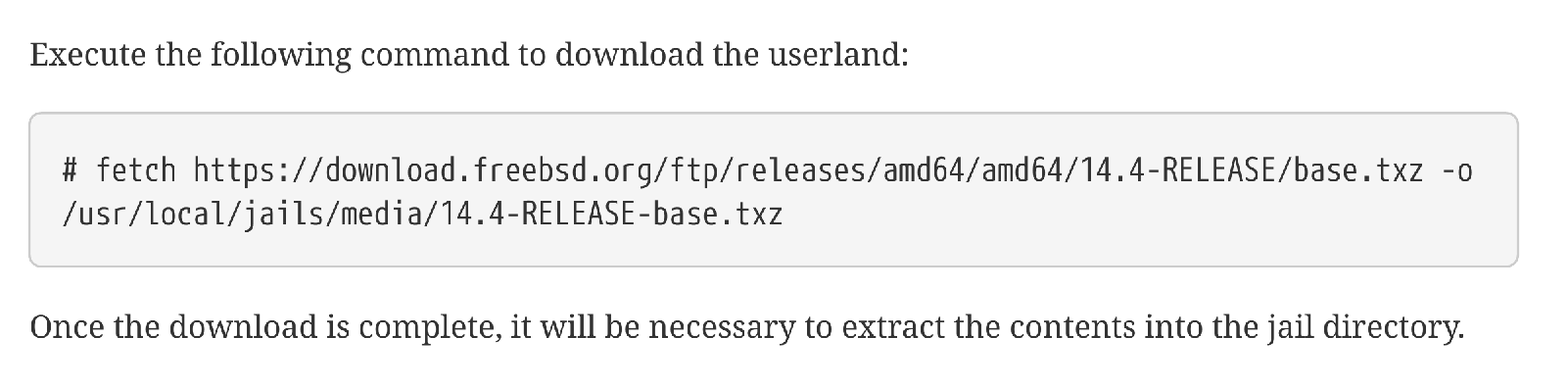 |
Unfortunately i don’t believe verification of the base.txz file might be possible now since as far as i can see, FreeBSD does not provide any signed checksum for this file.
Mitigation Strategies
If like me, you too are concerned about this, you can manually build your container images. For Linux, you can use the debootstrap package which has a --force-check-gpg option to enforce GPG verification.
debootstrap --force-check-gpg --include=dbus,systemd stable debian For FreeBSD jails, a workaround is to download the FreeBSD iso file, verify it using the signed checksums and extract the usr/bin/freebsd-dist/base.txz file from the ISO.
The distribution-gpg-keys repo, which contains the public keys of popular Linux distros and applications, have been packaged for a lot of the major Linux distributions, makes verification of the GPG signature easier.